- fast to operate
- simple to operate
- reliable
- difficult to tamper with
- simple auditing via the journal roll
- not vulnerable to computer viruses
Caution
SELLmatix has full strength security, which can be configured in many different ways
to provide the type of features you want, without causing obstruction.
Before you attempt to implement security, take care to read and understand this article and the options which are available to you. Careless attempts to implement security, without understanding the consequences, could result in locking yourself out of your system, incurring technical support charges.
Types of Operation
Security considerations vary widely from site to site. What is appropriate for one
site is often not suitable for another site. Broadly speaking, there are three
different types of operation that may be required:-
- Full Blown Security is typically used where operators are not trusted
and every security feature is required. In this case, POS needs to be run automatically
when the system starts, clerk logins are required, and without the appropriate access code
nothing can be done. Point of Sale is the only function performed on the system
and management does not want:-
- customers to wander up to an unattended POS computer and start playing with the system
- staff to be able to play games on the system
- other software to be run which could cause problems on the system
- other media to be inserted such as CD-ROM's which may contain viruses
- No Security is typically used where the owner(s) of the shop are the only people that use the system and have access to it. Since they trust themselves, security restrictions are pointless. Often these users will use the computer for other functions such as accounting, spreadsheets or word processing, and will switch to the POS software when they serve customers.
- Hybrid Security is used when operators are not trusted, but other applications need to run on the same computer which runs POS. Examples could include applications playing background music in a restaurant. In this case, full security needs to apply to the Point of Sale, and the operator needs to be able to access certain other applications (such as the music player), but unable to run other programs or tamper with the system.
It is important to note that full blown or hybrid security cannot be implemented in Point of Sale Software that runs on old operating systems such as Windows 95, 98, ME etc. This is because these operating systems do not have security and user accounts. Anyone that uses the system has the same rights as an Administrator in Windows NT and later.
Software the does implement security will not run on these old operating systems because for the software to implement security it has to make calls to the operating system which do not exist on these old operating systems.
In other words, if the software can run on Windows 95, 98 or ME, then it can not implement full blown or hybrid security. This is one of the reasons why SELLmatix requires Windows 2000 or later and will not run on older versions.
Certainly there are some things that can be done on these old systems to make it more difficult for someone hack, and many POS vendors with old legacy software will try to convince you otherwise, but a secure POS requires a secure operating system.
SELLmatix POS Security
SELLmatix is one of very few POS systems that enable you to operate security
the way that you want. There are two modes of operation. When run, POS
automatically starts in Sales Processing mode. To configure the POS
you need to switch to Menu Mode. In most configurations, switching to
Menu Mode requires supervisor access, and the supervisor
must Clerk On in order to switch mode.
Most of the Security features are configured in Menu Mode form the Tools->General Settings Menu. This dialog appears as follows:-
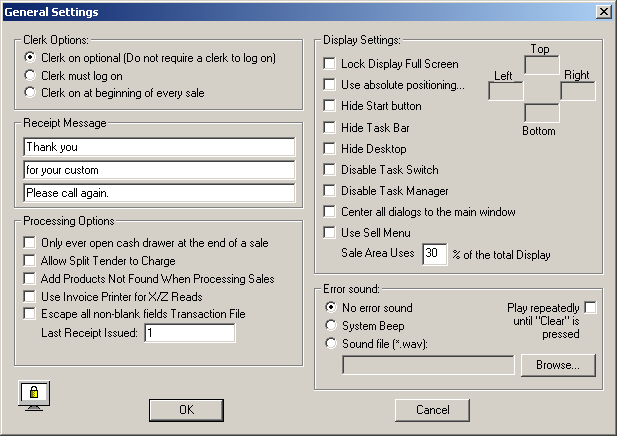
On the top left of this dialog are the clerking options.
- "Clerk on Optional" (unsecure mode) allows anyone to do anything. You might use this mode when setting up the system, or in cases where there is an owner/operator and no perceived risk of a customer walking up to the terminal and tampering with it.
- "Clerk must log in" means that a Clerk must log in, and that after login, they remain logged in until they log out, or another clerk logs in. This mode would typically be used where one person uses the POS terminal for a shift, and nobody else has physical access.
- "Clerk on at the beginning of every sale" means that when a sale is finalised, the system automatically logs of the clerk, and the clerk must log in again before processing the next sale. This would normally be used where multiple operators use the system at the same time, and is the most secure mode.
On the top right of the screen are a number of options for configuring security on the computer when the POS is processing Sales. Note that these options do not apply in Menu Mode when a supervisor is performing maintenance functions. To test these features, click the OK button and then choose File->Process Sales to see these options take effect.
- "Lock Display Full Screen" means that the POS display runs Full Screen, and its window cannot be resized or moved. This setting would be used in most POS systems.
- "Use Absolute Positioning" if checked, allows you to specify the screen coordinates where the POS window will be displayed.
When this box is checked, the POS display is shown at the coordinates entered, and it does not have a title bar and cannot be resized or moved.
This is useful where you do want some other software to be run at the same time as the POS, but you want to restrict what the operator can do.
Be careful when setting these coordinates because you could position the POS window in such a way that it could not be viewed or used. If that happens, check the Forum for a solution.
- "Hide Start Button" means that the Start button will disappear and new programs cannot be run. In this case, the Task Bar still appears, so an operator could still switch between programs that had been configured to run at Startup, but could not run anything else.
- "Hide Task Bar" removes the Task Bar. This means that the operator cannot use the task bar to change from one program to another.
- "Hide Desktop" hides the desktop so that there are no icons for the operator to click on to run other programs.
- "Disable Task Switch" disables keys on the keyboard that allow the user to switch from one task to another. These include the Alt Tab, Ctrl Esc combinations etc.
- "Disable Task Manager" prevents an operator from using the Ctrl-Alt-Del key combination to invoke Task manager and take control of the system.
Where security is important, however, you can restrict operators in whatever manner you choose you choose.
Other Considerations
You should also setup Windows security so that there are multiple logins, and that any automatic login does not
have administrator rights. The user profile for normal POS operation should have devices such as CD-ROM and floppy disk
drives disabled. Otherwise there is a chance of an operator putting in a CD-ROM to see what happens, and infecting the system with viruses.
SELLmatix POS "listens" for an incoming connection from SELLmatix Control, usually on Port 20,000. You will need to have Windows Firewall set to allow this connection. In most cases, there is no reason why a dedicated POS machine needs to allow any other connections. If setup this way there is little point in running a virus scanner all the time, and some virus scanners that check each disk read and write, when used on a low performance computer slow screen redraws somewhat.
With SELLmatix, you can have a POS system that is as stable, secure and reliable as a cash register, that also performs a range of other functions, because the software uses and requires the security features of Windows 2000 or later.
Changing Requirements
Every retailer installing a new POS system has certain security issues which
concern them and other security issues that they do not perceive as a threat.
Dealers report that within 12 months, as much as 80% of sites have their perceptions change about what constitutes a risk, and change their security settings as a result.
The incidents that lead to those changes in perception are rarely incidents that give the retailer pleasure. Surprisingly often, dealers have advised that certain precautions be taken, but the retailer did not perceive a risk.
Regardless of how you currently precieve your risk, bear in mind that your perception may change. Don't risk a POS system that may not meet your future security needs. With SELLmatix, the level of security you use is up to you, not a limitation in the software.